Scope of the Project
Phase 1 - completed
- Develop generic voting system models
Phase 2 - currently under review
- Analyze models to identify threats
- Use results of analysis to develop a threat assessment tool
- Tool will assist EAC and NIST in evaluating benefits and costs of proposed security requirements for VVSG 2.0
Seven types of attacks (threats) identified
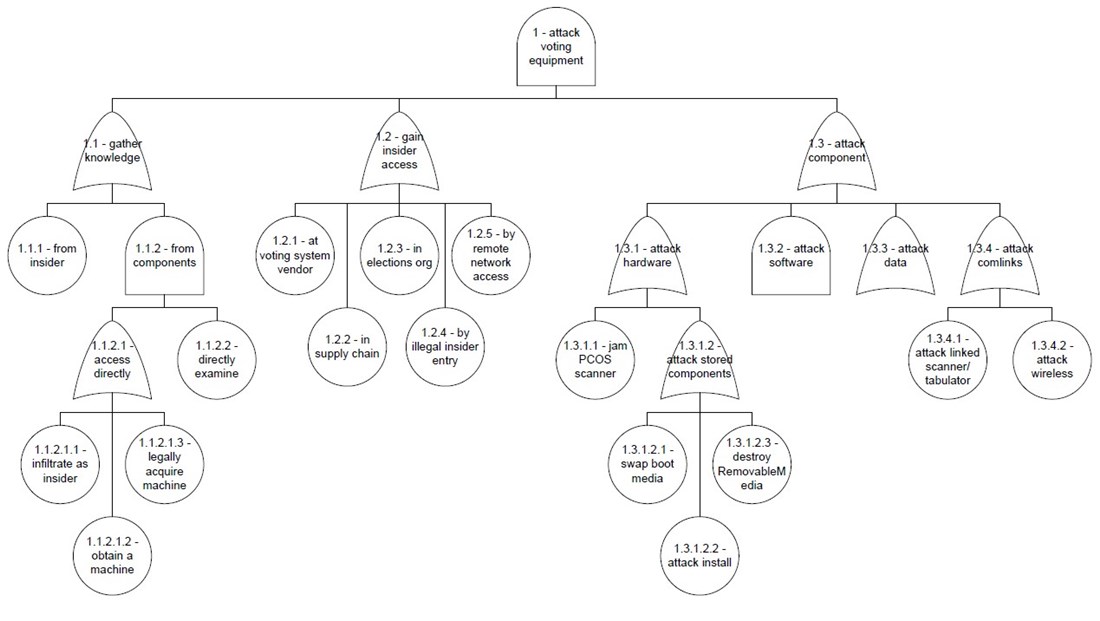
- Attack voting equipment
- Perform insider attack
- Subvert voting process
- Experience technical failure
- Commit errors in operations
- Attack audit
- Disrupt operations
Voting Technologies Assessed
Generic Technology Types
- Precinct Count Optical Scan (PCOS)
- Central Count Optical Scan (CCOS)
- Vote by Mail (VBM)
- Vote by Phone (VBP)
- Internet Voting (IV)
- Hand Counted Paper Ballots (HCPB)
Explanation of Terms
- A threat tree is a method to outline each type of attack (i.e., threat) and the steps required to exploit a potential system vulnerability
- A threat matrix documents additional information to more fully describe the nature of a threat action, its implications, and possible controls to prevent or mitigate its impact
Describing Threats
Technology threat information is described in three ways:
- A graphical threat tree
- A tabular threat tree
- A threat matrix
Optical Scan (PCOS)
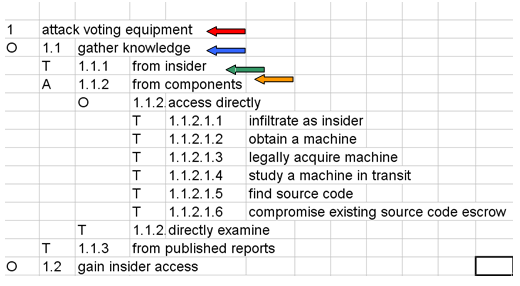
Tabular Threat Tree for Precinth Count Optical Scan (PCOS)
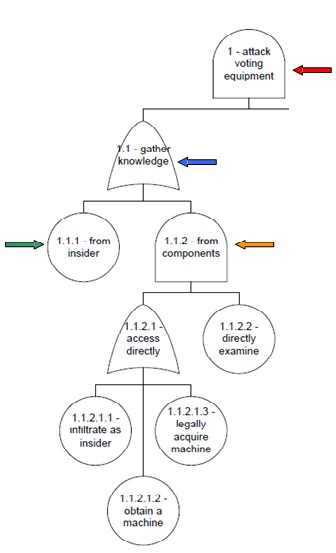
Comparison of Tabular and Graphical Trees
Comparison of Tabular and Graphical Trees
- Both trees display the same information
- To illustrate, the colored arrows point to the corresponding information in each tree
- By representing trees in both tabular and graphical formats, we accommodate both textual and visual information processing styles
Example of PCOS Threat Matrix
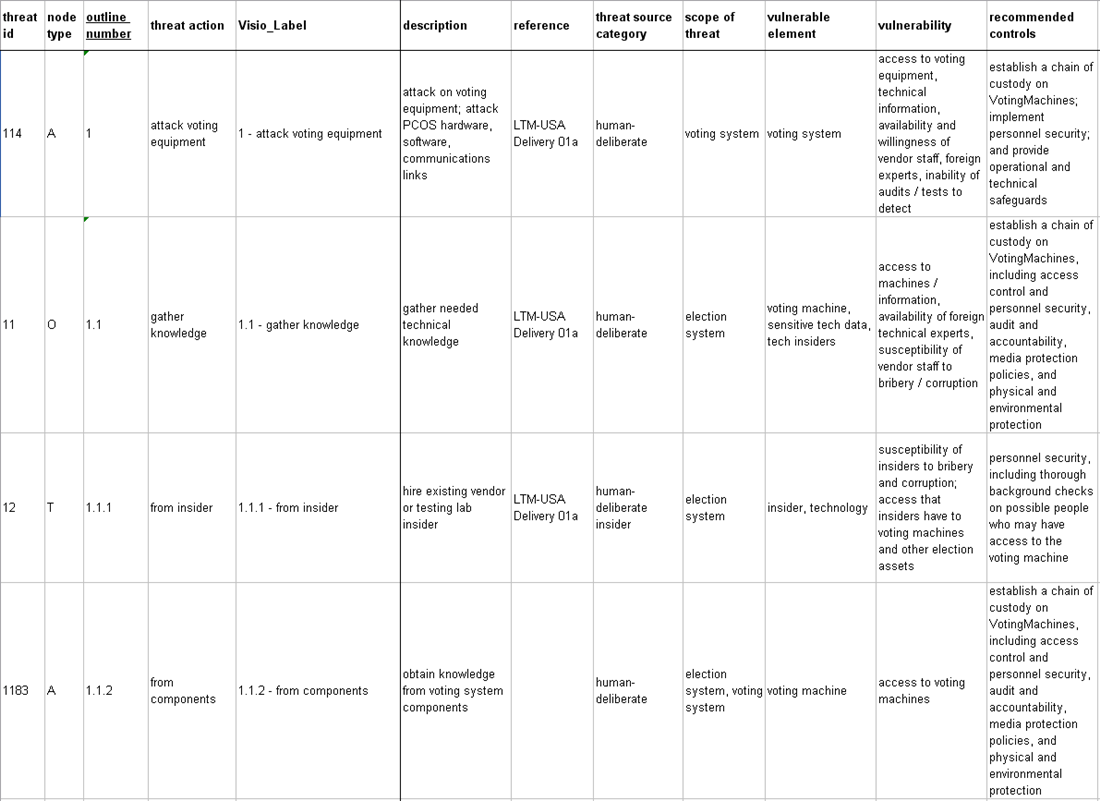
PCOS Threat Matrix Detail
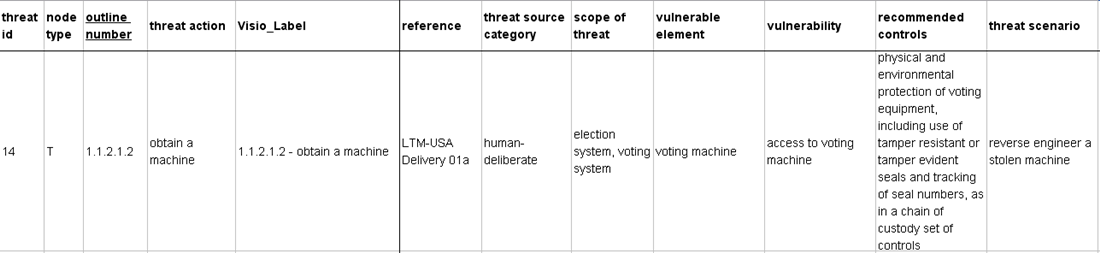
- This matrix detail illustrates the same PCOS Attack Voting Equipment example shown in the threat trees. The entries in the matrix describe the characteristics of each threat action identified in the threat trees.
Threat Instance Risk Analyzer (TIRA) Tool
TIRA is an automated tool that allows the user to quantify his/her professional intuition/judgment about the likelihood of a given threat happening and its potential impact on election operations. The analyst can rerun the analysis multiple times using different assumptions to see how much the result changes.
How to Use TIRA
-
Analyst creates a scenario by selecting threat instances from the trees
- Analyst uses TIRA worksheets to record scenario and assumptions
- Analyst assigns values for parameters of motivation, complexity, and impact
- Analyst runs TIRA simulation
- Result is a rank ordering of threats
Benefits of TIRA
- Organizes and structures thinking about risks
- Enables ‘apples to apples’ comparisons of different analysts assessments
- Allows analysis of hundreds of scenario variations in short period of time
- Permits analyst to make changes to threat matrices to create additional scenarios
Suggestions for Reviewing Threat Trees
-
Begin with a technology you are familiar with.
-
Compare what you know with what you see.
-
Identify any missing threat actions or other elements.
- Remember that TIRA uses these trees as inputs for creating scenarios. If something is missing from a tree it can’t be considered in the TIRA analysis.
Review Questions for Threat Matrices
- Do you understand the terms used in the column headings?
- Are there other threat actions you would add?
- Are there other mitigations / controls you would add?
- Would you change any entries in the cells of the matrix?
If your review time is limited, feedback on the overall matrix structure is more important than comments on the individual cells.